Azure MFA vs Conditional Access

Differencing behaviour between Azure MFA and Azure AD Conditional Access
- Azure MFA for Office 365
- Azure MFA (Full)
- Azure Conditional Access
- Registration of Credentials
- Word of Warning for NetScaler deployments
I wanted to take the time to clarify a few bits that have bitten some customers around the Azure MFA, Azure MFA for Office 365 and Conditional Access side of things and how they fit together
Azure MFA for Office 365
Azure MFA for Office 365 is not the same as “full” Azure MFA or Microsoft Azure Conditional Access. They may achieve the same basic result depending on the service in question, but they are different entitlements with different purposes and different scopes
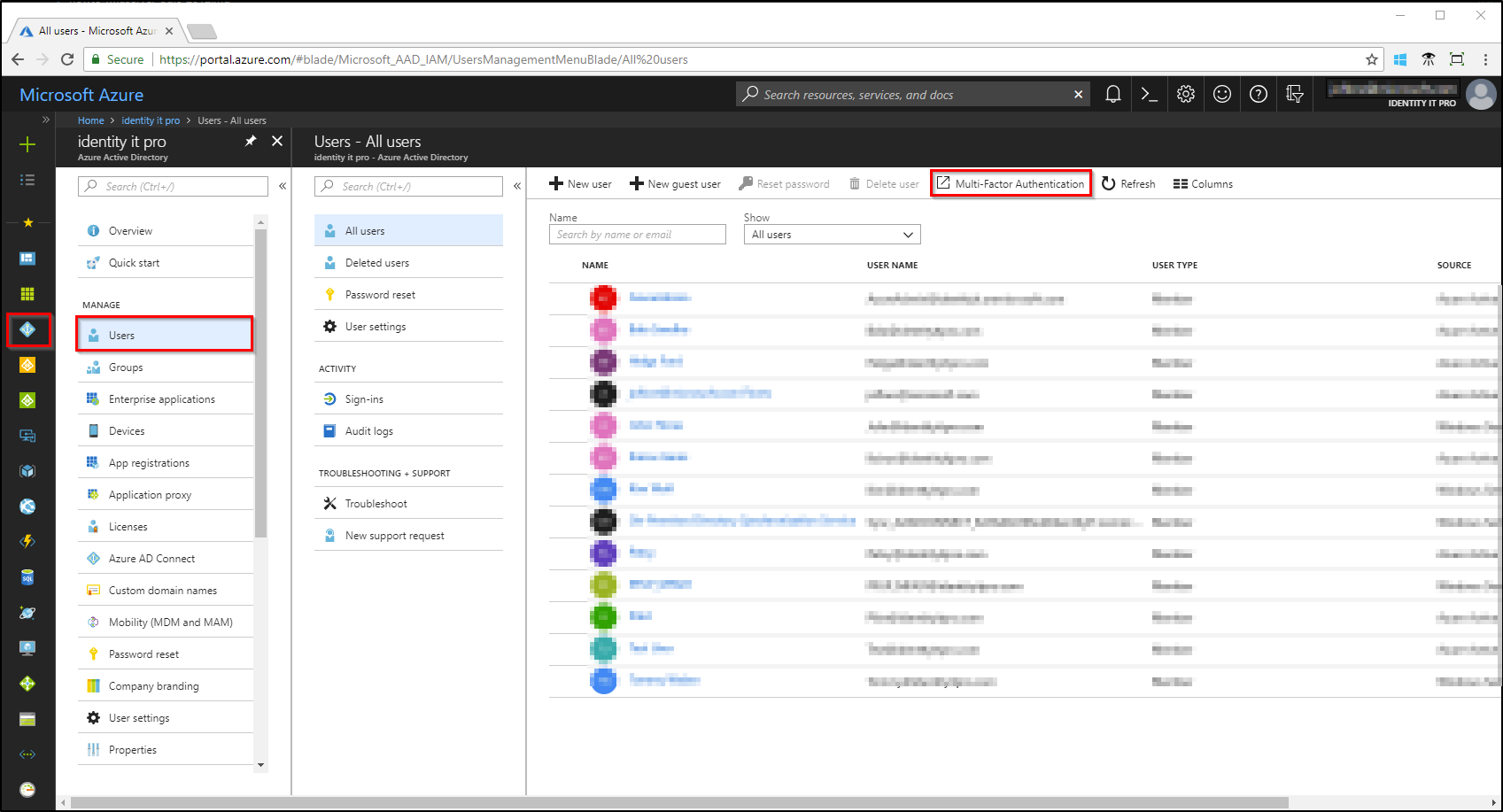
Azure MFA portal Access
Azure MFA for Office 365, which is driven out of the MFA Portal is the free offering available to all office 365 Customers. Its purpose is to protect your Office 365 Services using basic step up authentication. It provides services such as app passwords to get past applications that do not support modern authentication, which is not the most pleasant of all user experiences, and can have the security teams a little nervous. If you want to do more than just simple Office 365 based service protection, you need to move to a paid subscription of Azure MFA
Azure MFA (Full)
Azure Multi-Factor Authentication offers a rich set of capabilities. It provides additional configuration options via the Azure portal, advanced reporting, and support for a range of on-premises and cloud applications. Azure Multi-Factor Authentication is included in Azure Active Directory Premium plans, and can be deployed either in the cloud or on-premises. Azure Conditional Access will utilize the Azure MFA Service when called upon
Azure MFA Server Advanced Options
Azure Conditional Access
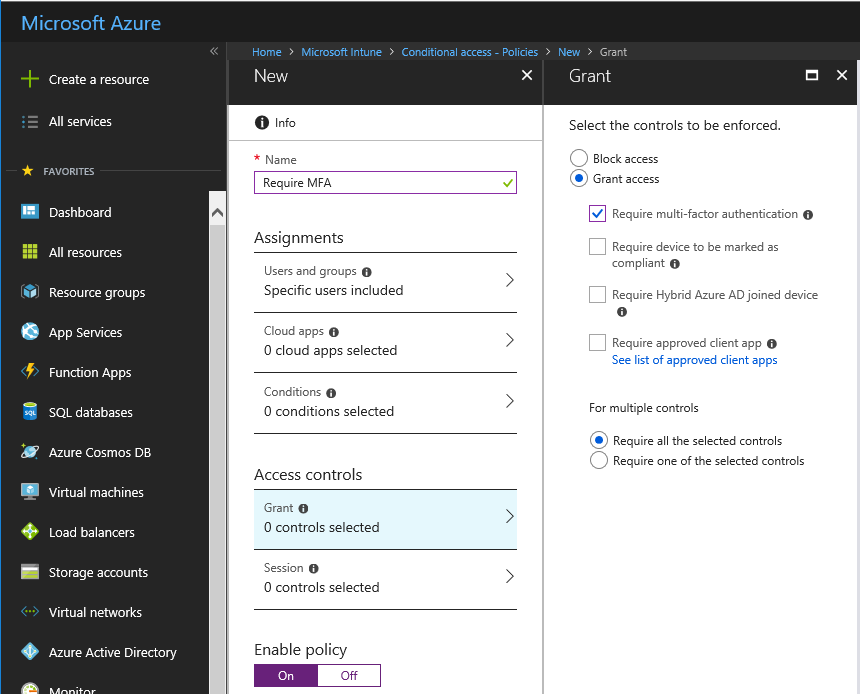
Azure Conditional Access is a service that requires an entitlement attained by either an Azure MFA Sku, EMS or AD Premium. It is the solution that allows you to write advanced conditions on any number of different scenarios, and can be extremely broad, or fine grained.
Conditional Access extends your authentication requirements out to federated 3rd party services so that you can protect not only your own assets, but access to those assets hosted in a SaaS style model. Conditional Access is not just Multi Factor Authentication. It can build access policies based on device management status (Intune or 3rd party MDM), application type, or a combination of many factors.
Registration of Credentials
What is extremely important to note, is that if you enable MFA via the MFA portal, you completely rub out the ability to utilize Conditional Access Policies. You must have the Azure MFA user state set to disabled, and a CA policy configured to require multi factor authentication for CA based settings to apply
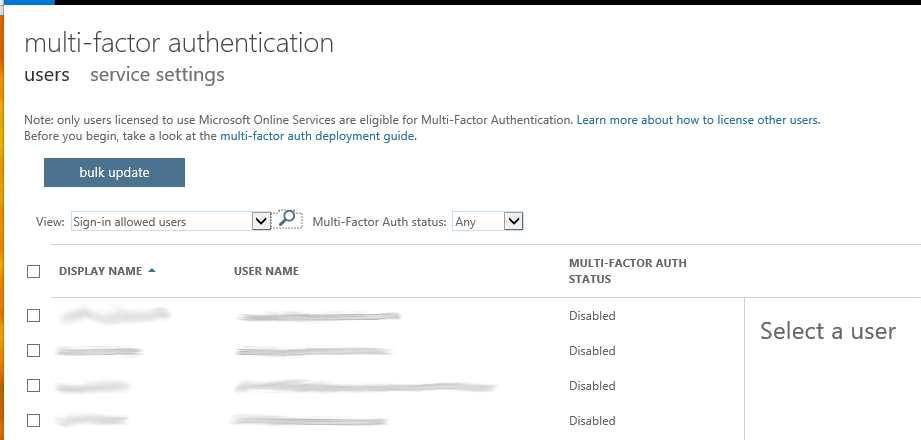
Azure MFA - Free - Disabled State
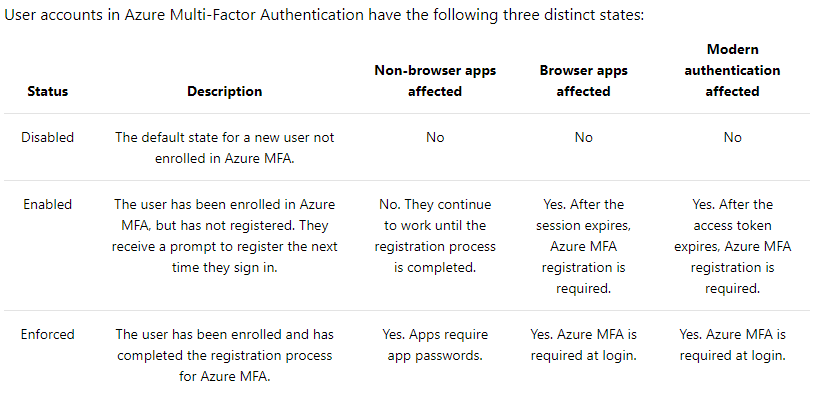
Microsoft provide some detail on the enrollment process and status when using Azure MFA
Azure MFA States
Registration into MFA is handled by either enabling MFA (Free) for the user, or making the user subject to a conditional access policy requirement. Both of these conditions will trigger the wizard for the user to enroll and manage their Authentication methods.
Azure Conditional Access Policies
Handling this process via Azure Conditional Access will not change the state in Azure MFA, it will still show as disabled for the user
Word of Warning for NetScaler deployments
When deploying Multi Factor with NetScaler against Azure MFA via either the NPS Extensions (RADIUS) or SAML against ADFS or Azure AD, it’s important to consider the impacts of Conditional Access vs Azure MFA. If you have plans, or your clients have plans to leverage the capability of Conditional Access moving forward, then its best to setup from the word go via Conditional Access Policies
George Spiers has a good article here for ADFS end to end
I had a write up here on using the NPS extensions a little while back
Aaron Parker has another nice write up here