AppLocker Script rules to maximise WEM logon benefits

Killing nasty logon scripts with AppLocker to let WEM do it’s job
Intro
One of the many benefits of WEM, and arguably the most important one, is the crazily reduced logon times you can gain by transferring actions and environmental setup tasks that would traditionally be handled by Group Policy Preferences or logon scripts. I wont go into detail about this here, as by now we mostly know the methodology on how and why WEM is a superior way to action these tasks.
What I tend to do in engagements that allow me to either green fields build, or implement within an existing environment, is ideally wipe out everything else in the environment that can effect what I want to WEM to deliver. To do this, I have a few tasks:
- Block inheritance on an OU with my target Workers in them, I also hunt down any GPO that is set to enforced and find out why as this will override blocking inheritance
- Ensure that Group Policy Loopback in replace mode is configured so that no pesky user GPO’s with nasty settings hit my environment
- Duplicate existing GPO’s that have preferences in them (user context) and convert them into WEM actions. I do this using Arjans PowerShell module that we worked on over Christmas break 2017. Once converted, I remove from the GPO so that it contains just ADMX based settings
- Convert any logon scripts held within GPO’s and create them as WEM External Tasks. Again this primarily actioned with Arjans PowerShell Module, or if there is only a couple, then I just manually create the task. I then remove them the GPO Objects
At this point I am left with an OU that I control, which has policies that are either new, or copied, cleaned of preferences and scripts and reviewed for appropriateness. This is a nice place to be but there is one outstanding component: Logon Scripts on the user account. This one is pretty narky as often we are not just working in a Citrix only environment, and these logon scripts effect the user no matter where they log in.
Enter AppLocker Script rules to the rescue.
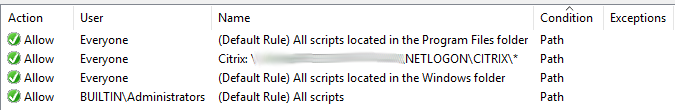
What I have found to work so far to date, is applying an AppLocker Script rule to block ALL scripts from running against the Citrix environments. This includes the logon scripts configured on the user accounts. I add a location (typically within the netlogon share) that I want WEM to be able execute scripts from, and simply add an allow rule for AppLocker to allow Scripts to process.
AppLocker Script - Path Rule
So far it works a treat, gives me what I want and ensures that by targeting only the Citrix OU’s with the rules, that I don’t hurt any other environment.